AI Overview:
Choosing the right Managed Service Provider (MSP) requires a clear look at technical expertise, service coverage, cybersecurity, SLAs, pricing models, and communication quality. This guide provides a simple evaluation framework with checklists, benchmarks, and comparison tables that help you judge providers on certifications, proactive maintenance, MDR/XDR security, uptime guarantees, response times, and total cost of ownership.
You’ll also learn how bundled services, strong SLAs, and a single point of contact improve reliability and reduce IT risk. The article explains how to verify vendor claims, negotiate contract terms, and use a free network assessment to identify priorities before signing. Following this framework turns MSP selection into an objective, measurable decision that strengthens security, reduces downtime, and keeps IT budgets predictable.
How to Select the Right Managed Service Provider: Your Complete MSP Evaluation and IT Partner Selection Guide
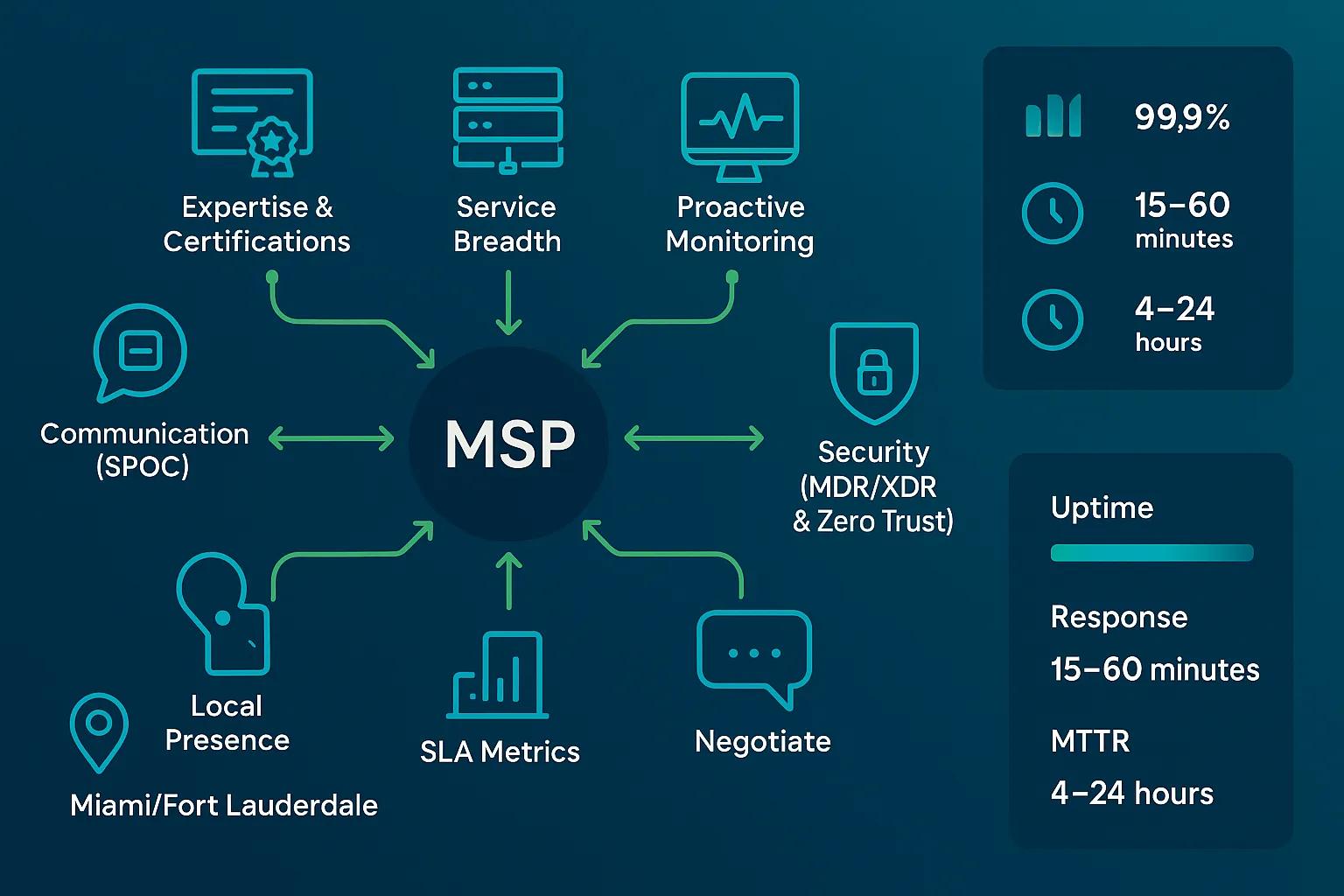
Choosing the right managed service provider (MSP) starts with a clear definition of what an MSP does and why that role matters for business continuity, cybersecurity, and predictable IT costs. An MSP is an outsourced IT partner that delivers managed IT services suchs as monitoring, patch management, backups, unified communications, and proactive maintenance to reduce downtime and align technology with business goals. This guide gives you a step-by-step MSP evaluation framework so you can compare providers on expertise, service breadth, SLAs, security, pricing models, and communication. You will learn concrete negotiation levers, sample SLA benchmarks, pricing comparisons for SMB budgets, and a cybersecurity checklist that ties MDR/XDR and zero-trust concepts to measurable outcomes. The article maps to practical decisions: how to prioritize certifications and vertical experience, how to read and enforce SLA terms, which security services to require, how pricing will affect total cost of ownership, and which communication structures enable a dependable IT partnership. Read on for checklists, EAV-style comparison tables, and questions to use during vendor interviews that help you select an MSP that fits your operational needs and budget.
What Are the Key Criteria for Choosing the Best Managed Service Provider?

A core set of evaluation criteria clarifies which MSPs are likely to deliver reliable, secure, and scalable managed IT services that align with business objectives. Start by assessing technical expertise, relevant industry experience, and formal certifications that indicate process maturity and vendor partnerships. Next evaluate the breadth of services—monitoring, patching, backups, managed cloud services, unified communications, and Microsoft 365 management—and the MSP’s ability to customize bundles and SLAs to your environment. Finally, weigh the provider’s posture on proactive maintenance, network monitoring, and local responsiveness because those factors determine uptime, mean time to repair, and long-term cost predictability. These evaluation elements set the foundation for comparing proposals and negotiating contract terms that protect your business outcomes.
Key criteria checklist you can use during vendor shortlisting:
- Expertise and certifications: Look for vendor and process certifications that match your tech stack and compliance needs.
- Breadth and customization of services: Ensure the MSP offers both core managed IT services and specialized options like Microsoft 365 management.
- Proactive operations and monitoring: Prefer providers with continuous monitoring, patching, and prevention-first approaches.
- Scalability and alignment with business goals: Confirm the MSP supports growth, cloud migrations, and evolving performance targets.
- Reputation, references, and local presence: Validate track record via client references and regional support capacity.
These checklist items focus your RFP discussions and prepare you to probe deeper into SLA specifics and security capabilities in the next sections.
How Do Expertise, Experience, and Certifications Impact MSP Selection?
Expertise, practical experience, and recognized certifications reduce delivery risk and speed onboarding by demonstrating process control and platform fluency. Certifications from major vendors and process frameworks (for example platform or service certifications and IT service management alignment) indicate baseline capability and integration experience, while vertical experience—such as work with healthcare or finance—signals familiarity with relevant compliance and workflow requirements. When evaluating claims, prioritize documented case studies, reference checks, and technical assessments that map the MSP’s prior work to your use cases. Beware of vendors who emphasize generic marketing claims without concrete examples, because real competence shows up in architecture diagrams, runbooks, and recovery plans rather than slogans. Understanding an MSP’s certifications and vertical experience helps you predict responsiveness and the quality of support during incidents, which ties directly to SLA performance and operational risk.
What Service Offerings and Customizations Should You Expect from an MSP?
A mature MSP offers a baseline of monitoring, patch management, helpdesk support, backups and disaster recovery, and network monitoring, plus managed cloud services and unified communications options. Look for explicit managed Microsoft 365 services, proactive endpoint protection, and packaged bundles that include regular maintenance windows and scheduled reporting. Customization matters: your MSP should be able to tailor SLAs by priority level, provide per-user or per-device plan options, and add specialized services such as migration support or compliance auditing. When comparing proposals, request a mapped service catalog showing responsibilities, tooling, escalation paths, and what’s included versus billed as an add-on. Clear scope definitions reduce billing surprises and ensure the MSP’s service delivery model aligns with your internal workflows and budget constraints.
How Do Service Level Agreements Define Your MSP’s Performance and Reliability?
Service Level Agreements (SLAs) codify the MSP’s commitments and translate technical metrics into business-level guarantees that protect availability, response, and resolution expectations. A strong SLA specifies guaranteed uptime for critical systems, response and resolution times by priority, escalation procedures, monitoring cadence, and remedies or penalties for noncompliance. SLAs should also define measurement methods, reporting frequency, and what constitutes excluded downtime or maintenance windows so you can reconcile performance with business KPIs. Reviewing SLA language early in negotiations ensures accountability and gives you concrete levers—financial or contractual—to enforce reliability. The following table maps essential SLA components to recommended benchmarks and business impact so you can compare vendor commitments side-by-side.
Intro: This table summarizes core SLA components, what each means, and the recommended benchmarks you should expect when negotiating an MSP contract.
| SLA Component | Definition | Recommended Benchmark / Business Impact |
|---|---|---|
| Guaranteed Uptime | Percentage of time critical services are available | 99.9% for core systems; improves customer-facing availability and reduces revenue risk |
| Response Time | Time to acknowledge incidents by priority level | 15–60 minutes for critical incidents; faster response reduces downtime exposure |
| Resolution Time | Time to restore service or provide workaround by priority | 4–24 hours for critical incidents depending on complexity; ties to MTTR reduction |
| Escalation Procedures | Defined steps and timelines for escalating unresolved issues | Clear escalation shortens resolution chains and ensures senior involvement |
| Penalties & Remedies | Financial credits or termination rights for SLA breaches | Defined credits and remediation maintain vendor accountability and business protection |
What Are the Essential SLA Components to Evaluate?
Evaluate SLA clauses that directly affect continuity and vendor accountability including uptime calculation, response and resolution targets by priority, escalation matrices, reporting and review cadence, and penalties or remedies for repeated breaches. Confirm how uptime is measured—by service, by region, or by component—and whether maintenance windows are pre-scheduled and excluded from uptime calculations. Response and resolution targets should be objective, tied to business priorities, and differentiated by severity level so critical outages receive immediate attention. Also require regular performance reports and quarterly reviews to ensure SLAs evolve with your environment. Reviewing these components clarifies expectations and gives you metrics to measure the MSP’s ongoing effectiveness.
The specification and quantification of SLAs are critical for bridging the gap between service providers and customers, ensuring clear expectations and accountability.
Service Level Agreements (SLAs): Specification, Principles, and Practices in Service Management
Software intensive systems (SIS) increasingly influence the ability of enterprises to be competitive in continuously changing market situations. The integration of these systems into organizations, and in particular the subsequent exploitation, maintenance and service activities, have become of utmost importance. Unfortunately the area of exploitation and operation, also known as service management, is still rather immature. Service management covers services such as performance and availability support, end-user and help desk support, education, and maintenance. One of the main concepts of service management is the Service Level Agreement (SLA). The goal of an SLA is to bridge the gap between service provider and users or customers. However, there exist many problems and unsolved questions regarding the specification and the quantification of SLAs. This paper addresses the specification of SLAs on the basis of three well-founded service management principles, respectively: ‘continuity in service management,’ the pit/shell principle of a service, and the principle of specifying the quality of both a service process and a service object. Finally, the paper addresses the validation of these principles in practice.
Specification of service level agreements: Problems, principles and practices, JJM Trienekens, 2004
How Can SLAs Protect Your Business and Ensure Quality IT Support?
SLAs protect business operations by converting service expectations into measurable obligations with defined consequences for shortfalls. Well-crafted SLAs include monitoring and reporting obligations that let you detect trend issues before they become outages, escalation paths that guarantee executive visibility for prolonged incidents, and credit mechanisms or termination clauses that provide financial recourse. During negotiations, align SLA metrics with business KPIs such as revenue-impacting application uptime and acceptable MTTR so penalties are meaningful and proportional. Finally, require periodic SLA reviews and a joint roadmap that updates targets as systems change—this enforces continuous improvement and keeps the MSP accountable to measurable outcomes.
Why Is Cybersecurity a Core Factor When Selecting a Managed IT Services Partner?
Cybersecurity determines your MSP’s ability to prevent, detect, and respond to threats that can cause data loss, regulatory exposure, and operational disruption; therefore security should be a core selection criterion. An MSP must provide layered defenses including endpoint protection, managed detection and response (MDR), backup and disaster recovery, network monitoring, and security policy management, plus guidance for implementing zero-trust principles. These services reduce dwell time, limit lateral movement, and enable rapid containment when incidents occur. Evaluate how the MSP integrates security into routine managed services—patching cadence, vulnerability scanning, and incident response workflows—because security that is bolted on after the fact delivers weaker protection than an integrated, proactive approach.
Intro to security services table: The table below compares key managed security capabilities, what they protect, and the outcomes you should expect from each service.
| Security Service | What it Protects / How it Works | When to Use / Expected Outcome |
|---|---|---|
| Endpoint Protection & EDR | Protects endpoints through prevention and detection; provides forensic telemetry | Use as baseline for all workstations and servers; reduces successful exploit rates |
| Managed Detection & Response (MDR) | Continuous threat hunting and active response by security analysts | Use when you need 24/7 detection and rapid containment; shortens dwell time |
| Extended Detection & Response (XDR) | Correlates signals across endpoints, network, and cloud for holistic detection | Use to reduce alert noise and improve cross-domain incident context |
| Backup & Disaster Recovery | Regular backups with tested restoration procedures | Use to recover from ransomware or data corruption; ensures business continuity |
| Zero-Trust Elements | Identity-centric controls, least-privilege access, and micro-segmentation | Use for high-risk environments and regulatory compliance; limits lateral movement |
What Cybersecurity Solutions Should an MSP Provide to Safeguard Your Business?

An effective MSP combines preventative tools—endpoint protection, patching, secure configuration—and detective capabilities such as MDR/XDR and continuous network monitoring to form a layered defense. Backups and tested disaster recovery plans are essential to recover from successful attacks, and policy-level services such as access controls, logging, and compliance reporting round out protection. Ask potential MSPs for examples of threat detection workflows, incident response playbooks, and evidence of tested recovery procedures. Integrated security services that tie into daily operations reduce friction and provide measurable improvements in mean time to detect and contain threats.
A framework for specifying and monitoring SLAs for web services, applicable to broader inter-domain management scenarios, emphasizes automated provisioning and objective QoS parameter measurement.
WSLA Framework: Specifying and Monitoring SLAs for Web Services
We describe a novel framework for specifying and monitoring Service Level Agreements (SLA) for Web Services. SLA monitoring and enforcement become increasingly important in a Web Service environment where enterprise applications and services rely on services that may be subscribed dynamically and on-demand. For economic and practical reasons, we want an automated provisioning process for both the service itself as well as the SLA managment system that measures and monitors the QoS parameters, checks the agreed-upon service levels, and reports violations to the authorized parties involved in the SLA management process. Our approach to these issues is presented in this paper. TheWeb Service Level Agreement (WSLA)framework is targeted at defining and monitoring SLAs for Web Services. Although WSLA has been designed for a Web Services environment, it is applicable as well to any inter-domain management scenario, such as business process and service management, or the management of networks, systems and applications in general. The WSLA framework consists of a flexible and extensible language based on XML Schema and a runtime architecture comprising several SLA monitoring services, which may be outsourced to third parties to ensure a maximum of objectivity. WSLA enables service customers and providers to unambiguously define a wide variety of SLAs, specify the SLA parameters and the way they are measured, and relate them to managed resource instrumentations. Upon receipt of an SLA specification, the WSLA monitoring services are automatically configured to enforce the SLA. An implementation of the WSLA framework, termedSLA Compliance Monitor, is publicly available as part of the IBM Web Services Toolkit.
The WSLA framework: Specifying and monitoring service level agreements for web services, A Keller, 2003
How Do Advanced Security Services Like MDR and Zero-Trust Frameworks Enhance Protection?
MDR offers dedicated security expertise—human analysts combined with tooling—that hunts for threats, validates alerts, and conducts containment actions to reduce dwell time and limit impact. XDR extends those capabilities by correlating telemetry across endpoints, network, and cloud to provide richer context and faster root-cause analysis. Zero-trust frameworks, by enforcing least-privilege access and continuous identity verification, reduce the attack surface and stop lateral propagation of breaches. Together, these advanced services transform reactive incident response into proactive risk reduction and align security outcomes with business continuity goals.
Note on local assessment: For organizations seeking a security-focused technical baseline, some managed IT service providers include a free network assessment to identify configuration weaknesses and quick wins for risk reduction. Barlop Business Systems, which provides managed IT services, managed cybersecurity, unified communications, and Microsoft 365 services in the Miami/Fort Lauderdale area, explicitly lists proactive cybersecurity and a free network assessment among its offerings. That kind of local assessment can help you prioritize remediation tasks and shape SLA expectations tailored to regional operational needs.
What Are the Common MSP Pricing Models and How Do They Affect Your IT Budget?
MSP pricing models influence predictability, scalability, and the incentives for preventative maintenance versus reactive support, so understanding billing methods is critical for accurate budgeting. Common approaches include per-user, per-device, tiered, and flat-rate models, each with trade-offs around predictability and cost control. Bundled agreements can simplify procurement but require careful SLA alignment to avoid hidden fees for prioritized services. Use the table below to compare pricing models with practical SMB cost examples so you can see how each model impacts monthly spend and scaling behavior.
Intro to pricing table: This table compares common pricing models, how they’re billed, and pros/cons with SMB cost examples to illustrate likely monthly impacts.
| Pricing Model | Billing Method / Best for | Pros, Cons & SMB Cost Example |
|---|---|---|
| Per-User | Billed per active user; best for steady headcount | Predictable for SaaS-heavy teams; example $50/user/mo for 20 users = $1,000/mo; can be inefficient for device-heavy roles |
| Per-Device | Billed per managed device; best for device-centric environments | Simple for fixed hardware counts; example $40/device/mo for 30 devices = $1,200/mo; scales poorly with BYOD |
| Tiered | Service tiers with limits; best for mixed needs | Balances features and cost; example Tier 2 at $2,000/mo covers X users and Y devices; complexity in overage rules |
| Flat-Rate / All-Inclusive | One monthly fee for defined scope; best for predictable budgets | Predictable TCO and incentivizes prevention; example $3,000/mo for full coverage; may include limits on project work |
How Do Per-User, Per-Device, Tiered, and Flat-Rate Pricing Models Compare?
Per-user billing simplifies SaaS and account management but may overcharge for users who require few managed resources. Per-device billing aligns cost with hardware counts but complicates BYOD and remote work. Tiered models offer feature bundles for predictable service levels but can hide overage fees for out-of-scope services. Flat-rate or all-inclusive models maximize predictability and encourage preventative maintenance, though they may place limits on major projects unless negotiated separately. Evaluate real-world scenarios—headcount growth, device churn, and expected project work—to choose the model that minimizes total cost of ownership while preserving flexibility.
Intro to pricing list and summary: A short list of ways bundled agreements can maximize value follows, then a summary paragraph that ties bundling to ROI and negotiation tactics.
- Bundling helpdesk, monitoring, and backups simplifies vendor management and reduces administrative overhead.
- Including security add-ons like MDR or endpoint protection in a bundle often lowers marginal cost versus standalone contracts.
- Negotiating fixed rates for routine work while carving out project scoping for specific upgrades keeps budgets predictable.
- Asking for transparent overage rates and annual review clauses prevents bill surprises and preserves negotiating leverage.
Bundled agreements, when structured with clear SLAs and project carve-outs, typically deliver lower TCO and better vendor alignment than multiple point contracts. Make sure bundled SLAs explicitly include the security and availability metrics your business depends on.
How Can Bundled and Affordable Service Agreements Maximize Value?
Bundled agreements consolidate services into one predictable payment and encourage the MSP to invest in monitoring and preventative measures that reduce incident frequency. To maximize value, require bundled SLAs that cover incident priorities, reporting, and remediation workflows, and ensure project work beyond the bundle is quoted transparently. Ask for annual reviews that adjust the bundle for growth and technology changes to avoid paying for unused services or suffering gaps as priorities evolve. Well-negotiated bundles provide predictable budgeting, simplified vendor coordination, and better alignment of incentives toward uptime and security.
How Does a Proactive IT Partner Add Value Beyond Traditional Break-Fix Support?
A proactive IT partner focuses on prevention—continuous monitoring, patch management, vulnerability remediation, and capacity planning—rather than simply repairing systems after failures, which leads to measurable reductions in downtime and IT-related business disruption. Proactive services identify trends and latent failures early, apply controlled remediations, and implement improvements that lower the frequency and impact of incidents. This approach yields lower mean time to repair, reduced operational costs over time, and better alignment of IT with strategic initiatives. The next subsections explain operational metrics and how local presence amplifies proactive benefits.
What Are the Benefits of Proactive Maintenance and Network Monitoring?
Proactive maintenance and network monitoring detect anomalies, apply patches, and remediate vulnerabilities before they escalate into outages or breaches, improving reliability and reducing emergency support costs. Continuous monitoring shortens detection windows, which decreases mean time to detect and mean time to contain incidents, and scheduled maintenance prevents cascading failures. Proactive practices also enable capacity planning and performance tuning, reducing the need for costly reactive upgrades. Organizations that adopt proactive managed IT services typically experience fewer critical incidents, improved end-user satisfaction, and more predictable IT budgets, which supports operational stability and strategic growth.
How Does Local Presence, Like Barlop’s Miami/Fort Lauderdale Support, Enhance Your MSP Experience?
Local presence improves responsiveness, enables on-site interventions, and provides contextual knowledge about regional compliance and connectivity constraints, which can be critical when rapid escalation or physical access is needed. A local MSP can dispatch technicians for hardware issues, coordinate with regional carriers, and offer face-to-face planning sessions that strengthen the ongoing partnership. Barlop Business Systems lists Miami/Fort Lauderdale as a primary service area and highlights offerings such as managed IT services, unified communications, and Microsoft 365 management along with UVPs like proactive maintenance, world-class network support, and a single point of contact. Local support paired with bundled, affordable service agreements can shorten resolution times and improve accountability compared with distant or remote-only providers.
How Can Effective Communication and Support Improve Your Managed IT Services Partnership?
Effective communication and structured support are the operational glue that makes an MSP relationship predictable and efficient; they determine how quickly incidents are triaged, how well strategic projects are coordinated, and how transparent performance reporting is to stakeholders. Assessing communication channels, reporting cadence, escalation paths, and account management clarity helps you select a partner that aligns with your governance and oversight needs. A single point of contact simplifies coordination, reduces misdirected work, and speeds escalation, while regular business reviews ensure SLAs and roadmaps remain aligned to evolving priorities. The following lists offer practical questions to use during vendor interviews and explain the advantages of a single point of contact.
Intro: Use these vendor interview questions to evaluate communication and support quality; each item helps reveal operational maturity and transparency.
- How frequently do you deliver performance and security reports, and what metrics do they include?
- What are your defined escalation paths for critical incidents, and how are senior engineers engaged?
- Who will be our account manager or single point of contact, and what are their responsibilities?
- How do you handle out-of-scope requests and project work versus managed services under the agreement?
What Questions Should You Ask to Assess MSP Communication and Support Quality?
Ask about reporting cadence, escalation matrices, the identity and role of your account manager, and examples of how communication worked during a prior major incident. Request sample reports and a description of how tickets are triaged and escalated by priority. Clarify who signs off on changes and how planned maintenance is communicated and approved. Finally, probe how the MSP measures customer satisfaction and whether they conduct regular business reviews to align IT investment with your company goals. These questions reveal the operational discipline behind the MSP’s support model so you can choose a partner that communicates proactively and reliably.
How Does a Single Point of Contact Simplify Your IT Management?
A dedicated account manager or single point of contact (SPOC) centralizes communication, consolidates technical knowledge about your environment, and reduces administrative friction for change approvals and incident escalations. The SPOC coordinates between technical teams, vendors, and your internal stakeholders, ensuring issues progress efficiently through resolution and that strategic projects have clear ownership. This arrangement shortens decision cycles, avoids duplicated communications, and improves accountability because expectations and follow-ups go through a known person. When combined with documented SLAs and regular reviews, a single point of contact makes the MSP relationship far more predictable and easier to manage operationally.
For organizations looking to validate their environment and align on remediation priorities, a free network assessment can be a useful first step. Some managed IT service providers explicitly include a complementary assessment to identify risks and produce a remediation roadmap. Barlop Business Systems highlights proactive maintenance, enhanced network management and monitoring, and a free network assessment as part of its managed IT services offering in the Miami/Fort Lauderdale area, providing a practical starting point for locally based businesses to evaluate their managed services options.
- Assessment Benefits: A free network assessment identifies misconfigurations and high-priority risks without initial procurement commitment.
- Actionable Roadmap: Deliverables typically include prioritized remediation tasks, cost estimates, and suggested SLA targets.
- Negotiation Leverage: Use assessment findings to negotiate precise SLA terms and targeted service bundles.
- Local Context: Regional assessments consider local carrier constraints and compliance factors relevant to your area.
How to Select the Right Managed Service Provider: Your Complete MSP Evaluation and IT Partner Selection Guide
This last section reiterates the practical path forward and ties assessment to vendor selection without adding a new heading. Use the evaluation checklist, SLA benchmarks, security service comparisons, pricing model examples, and communication questions above to create an objective scoring sheet for vendor proposals. Score vendors on expertise, service coverage, SLA strength, security integration, pricing alignment, and communication quality, then weight items according to your business priorities. For businesses in the Miami/Fort Lauderdale area seeking a local, proactive partner with bundled service options and a single point of contact, a free network assessment can help validate priorities and accelerate onboarding. Barlop Business Systems is one example of a managed IT and cybersecurity provider that promotes proactive maintenance, world-class network support, unified communications, and Microsoft 365 services along with a free network assessment to begin the evaluation process.
The quality of IT hardware service support can be significantly enhanced by adopting Service Level Agreements (SLAs), which act as contracts defining service metrics and penalties for non-compliance.
Adopting Service Level Agreements (SLAs) for IT Hardware Service Support Quality
Service Level Agreement (SLA) is a contract between a service provider and different levels of users in the organization. SLA lays out the metrics by which a service is measured, as well as penalties should the expected service levels are not met. SLA reduces the amount of job schedule based on IT support services and transfers all IT-related problems to the service provider. Existing SLA approaches have several limitations including pricing strategy, incident handling, and documentation. A more “customized” approach needed for SLA Hardware based on the organization’s mission and vision. Adopting the SLA also act as a KPI (Knowledge Performance Index) for the internal services that reflect back to the company performance and users experiences. This paper proposes a research framework study for such as framework based on strong theoretical foundation and industry best practice and can be apply to organization or company that does not have the SLA system on the IT service
Adopting of Service Level Agreement (SLA) in enhancing the quality of IT hardware service support, AA Ahmad, 2020
- Create a scoring matrix: Weight technical fit, security, SLA rigor, pricing, and communication to compare proposals objectively.
- Validate claims: Use reference checks and the MSP’s technical artifacts to confirm competence and response behavior.
- Negotiate SLAs and bundles: Translate assessment findings into enforceable SLA metrics and clear scope for bundled agreements.
- Start with an assessment: Use a free network assessment to clarify priorities and quantify remediation needs before signing long-term contracts.
Using this systematic approach converts vendor selection from a subjective process into a measured procurement decision that protects uptime, reduces cyber risk, and keeps IT budgets predictable while allowing for growth and change.




